FullEventLogView比eventvwr的优势就不赘言了
http://www.nirsoft.net/utils/full_event_log_view.html
说下使用技巧
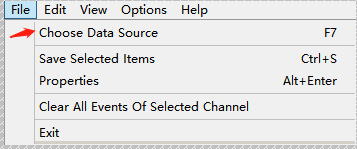
外部机器.evtx的分析用它非常方便,.evtx一般在C:\Windows\System32\winevt\Logs目录,要分析哪台机器的,把日志拿过来,在FullEventLogView里如下图指定数据源,数据源里的文件后缀用*.evtx
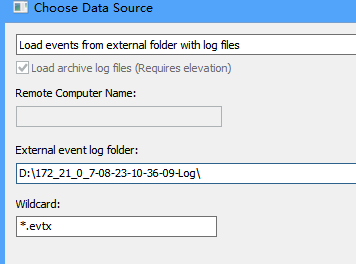
指定条件分析很方便:
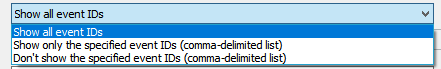
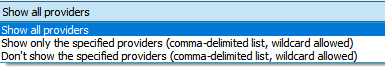
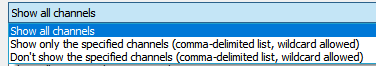
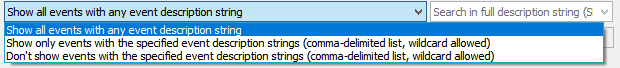
条件维度如下图比较多,时间、事件级别、事件ID、来源、描述等
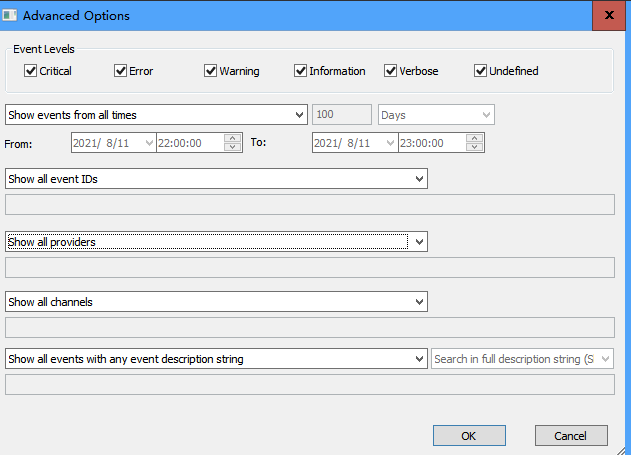
可以指定条件正向过滤,也可以指定条件反向过滤
扩展:
端口耗尽、tcpip相关日志
4227,4231,4266
开关机相关的事件ID
12,13,6005,6006,6008,41,1074
ProviderName:Microsoft-Windows-User Profiles Service
1530,1531,1532
ProviderName:Windows Error Reporting
1001
激活相关的事件ID
8197,8198,12288,12289
这样过滤(一般来说用事件ID过滤效率高,过滤得快,如果用description里的字符串过滤,效率会差一些,过滤得慢)
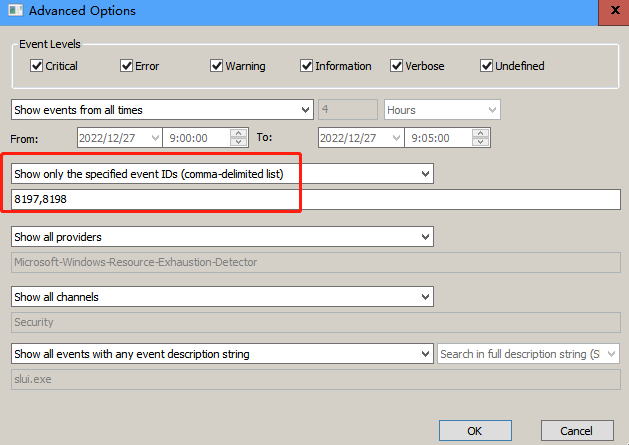
或者
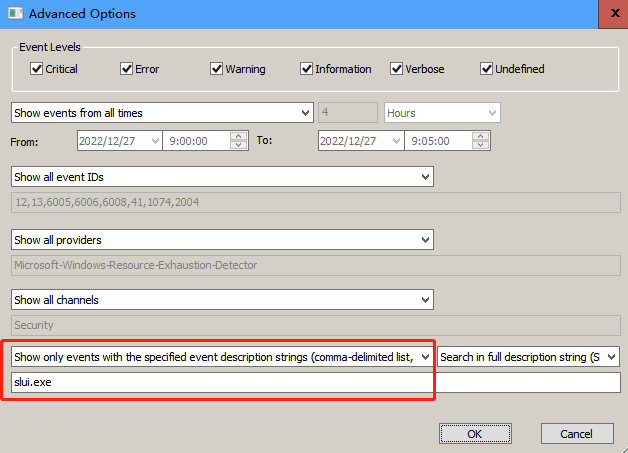
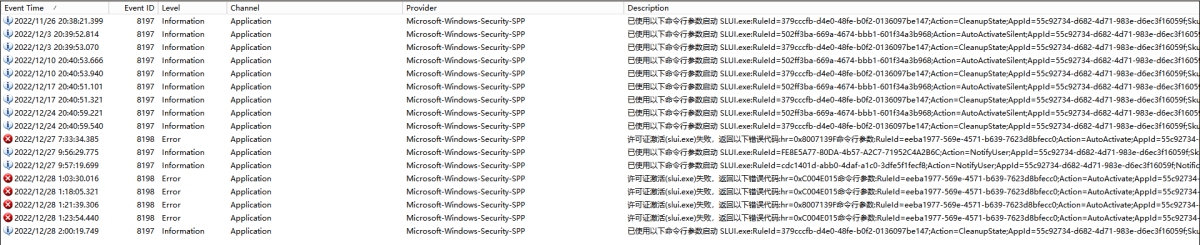
powershell命令过滤日志举例:
tcpip来源的日志4227,4231,4266(如过滤到,则需要放大tcp动态端口范围、缩短timewait回收时间)
Get-EventLog -LogName System -Source Tcpip -ErrorAction SilentlyContinue |Where-Object {$_.EventID -eq “4227” -or $_.EventID -eq “4231” -or $_.EventID -eq “4266”} |FT TimeGenerated,EventID,EntryType,Source,Message
Get-WinEvent -FilterHashtable @{logname=’System’;id=@(4227,4232,4266);StartTime=(Get-Date).AddDays(-10)} -ErrorAction SilentlyContinue |Sort-Object -Property TimeCreated
Get-WinEvent -FilterHashtable @{logname=’System’;source=’Tcpip’;id=@(4227,4232,4266);StartTime=(Get-Date).AddDays(-10)} -ErrorAction SilentlyContinue |Sort-Object -Property TimeCreated
Get-WinEvent -FilterHashtable @{logname=’System’;id=@(12,6005,6006,13,6008,41,1074);StartTime=”2021-07-27 00:00:00″;EndTime=”2021-07-28 00:00:00″}
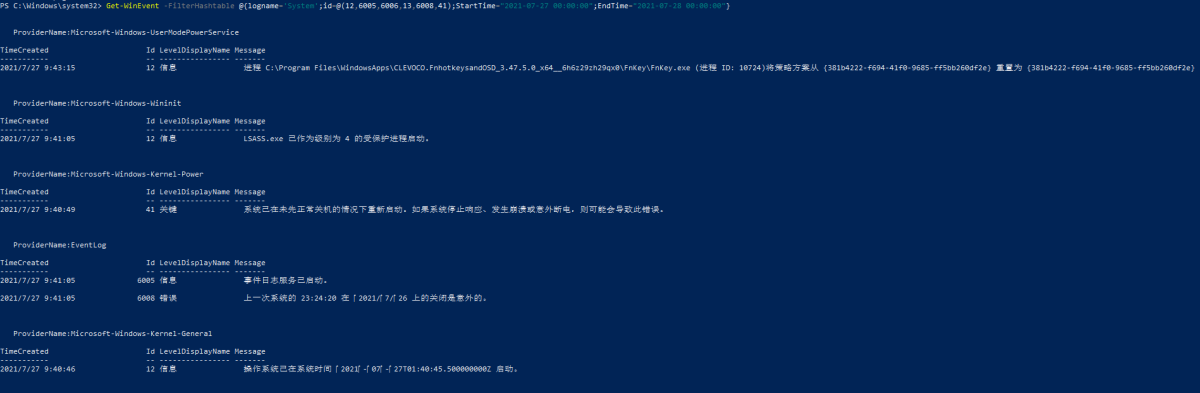
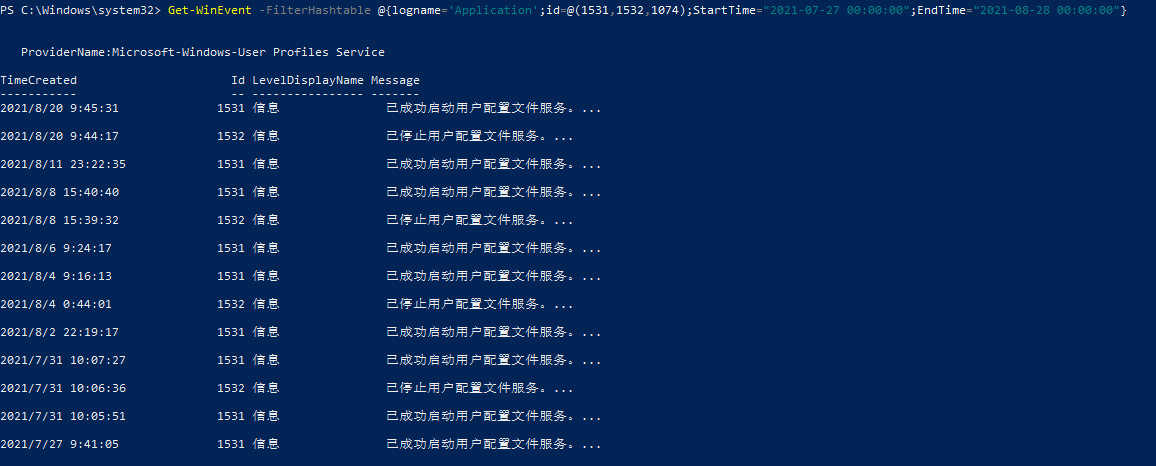
Get-WinEvent -FilterHashtable @{logname=’Application’;id=@(1530,1531,1532,1001);StartTime=”2021-07-27 00:00:00″;EndTime=”2021-08-28 00:00:00″}
其他例子:
#查最近1天的开关机、重启记录
Get-WinEvent -FilterHashtable @{logname=’System’;id=@(12,13,6005,6006,6008,1074,41);StartTime=(Get-Date).AddDays(-1)} -ErrorAction SilentlyContinue |Sort-Object -Property TimeCreated
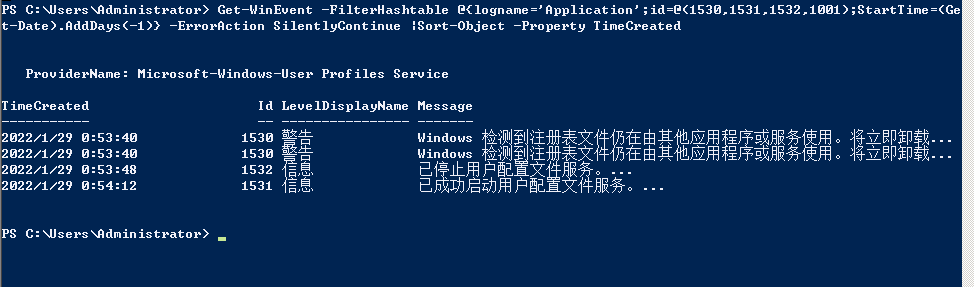
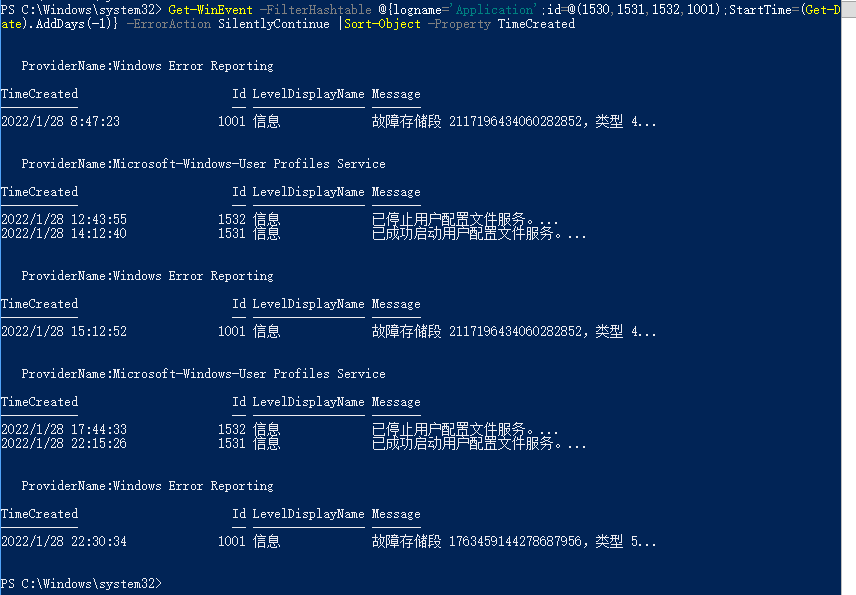
#查最近1天登录相关的记录和Application报错
Get-WinEvent -FilterHashtable @{logname=’Application’;id=@(1530,1531,1532,1001);StartTime=(Get-Date).AddDays(-1)} -ErrorAction SilentlyContinue |Sort-Object -Property TimeCreated
#查最近1天的暴力破解记录
Get-WinEvent -FilterHashtable @{logname=’Security’;id=@(4625);StartTime=(Get-Date).AddDays(-1)} -ErrorAction SilentlyContinue |Sort-Object -Property TimeCreated
